Cloud Foundry Security Overview
Preventing security threats require careful and thoughtful consideration, and Cloud Foundry does its best to protect user applications and data. Among measures that help the platform to keep key information safe are role-based access control, protection for applications and service broker integration, and an audit trail. Learn more about how the PaaS architecture meets security requirements from the article.
Security principles
Setting access controls and isolating user applications and data are the core security principles of Cloud Foundry.
To eliminate security risks, Cloud Foundry:
- Implements role-based access control
- Secures application artifacts
- Ensures security for service broker integration
- Provides an audit trail
System access is restricted to authorized users. A user can have one or more roles giving permissions in an org and within specific spaces in that org.
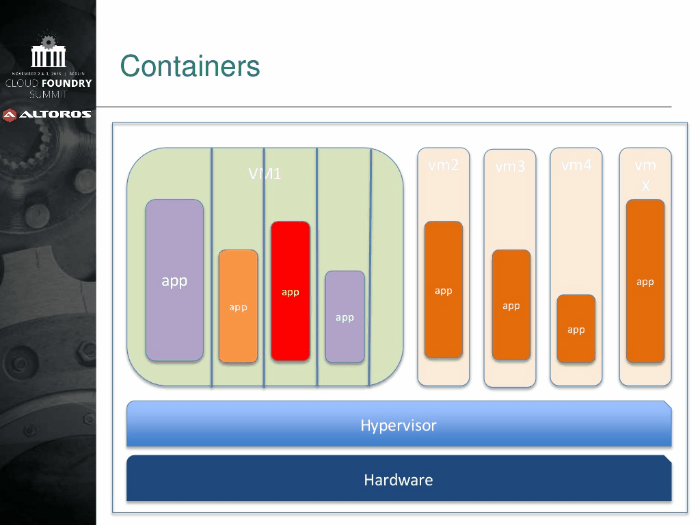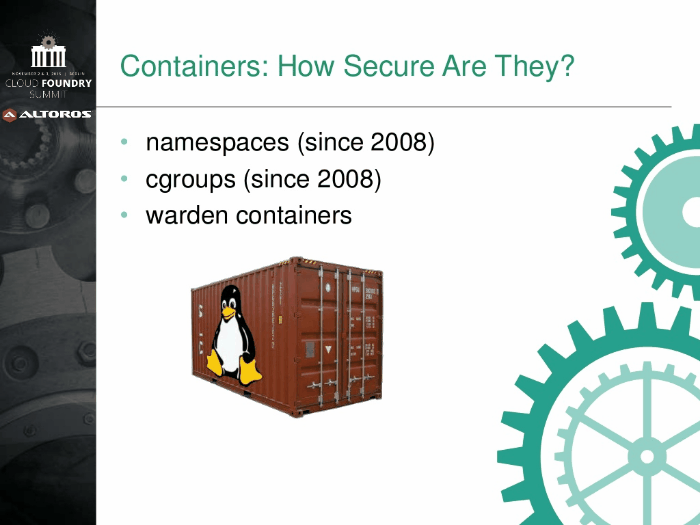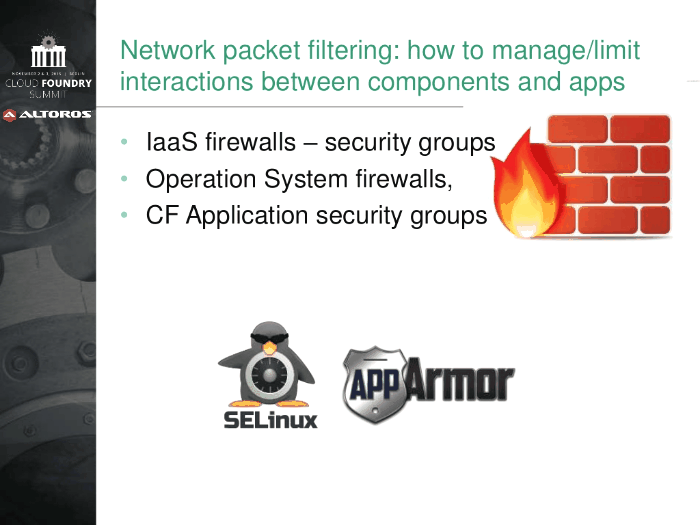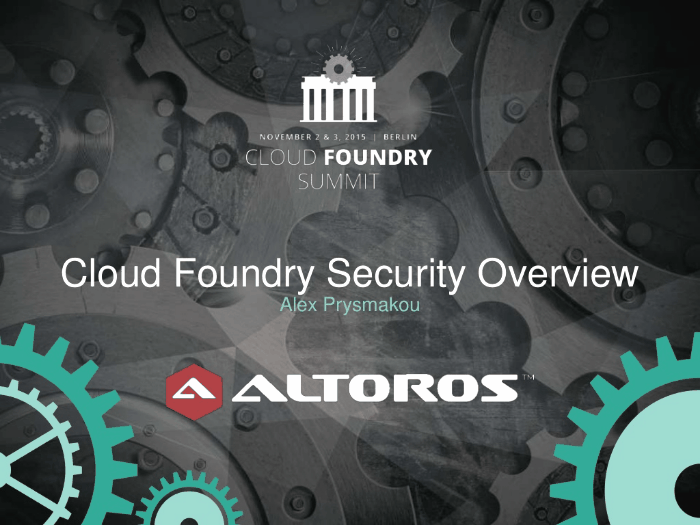
In addition to a RBAC approach, Cloud Foundry isolates applications with containers, stores application configuration—environment variables and service credentials—in an encrypted database table, and works with network traffic rules. For more information, go to CF Docs.
The platform authenticates all requests with a service broker when making API calls and rejects broker registrations that do not have a username and password. It is also possible to connect to a broker using SSL.
The records are available for Cloud Foundry components, applications, and BOSH.
Cloud Foundry and the outside world
When the PaaS components run on virtual machines within a VLAN, the resources visible for external networks are:
- Load balancer
- NAT (optionally)
- Jumpbox (optionally)
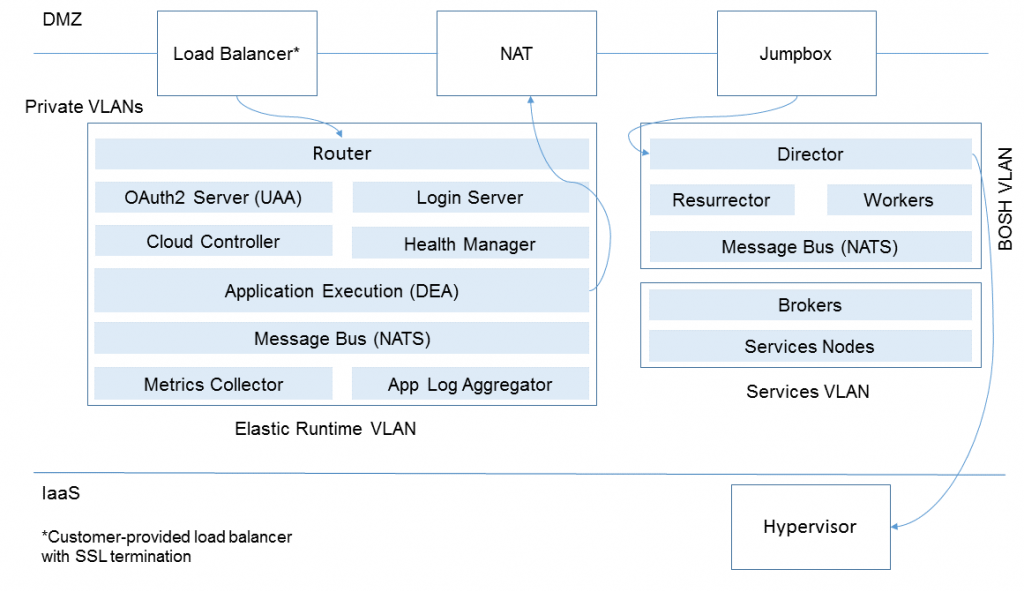
In this schema, the platform communication with the outside world happens through a load balancer passing requests to the Cloud Foundry Router(s) so that the application execution component is not exposed.
Network traffic rules
On the component VMs, Cloud Foundry uses Linux iptables. It is possible to configure network traffic rules to:
- prevent system access from external networks
- control outbound traffic from applications
- prohibit communication between system components and applications
Cloud Foundry Docs provide a detailed security overview.
Interested in exploring Cloud Foundry security further? Dive into the details with our blog post series: