Cloud Foundry Advisory Board Meeting, Nov 2018: VMs vs. Containers

The highlight of this month’s Cloud Foundry Community Advisory Board (CAB) call were the test results of a benchmark—comparing virtual machines (VMs) with containers—conducted by SUSE. Overall, the tests showed both installations to be stable, at similar costs albeit with a few apples versus oranges in how they were deployed.
The regular reports on the ecosystem projects were also submitted by the core teams.
Performance benchmark: VMs against containers
Vlad Iovanov from SUSE shared the results of the benchmark that compared performance of VMs to containers. His presentation was based on the session he and his colleague Jeff Hobbs delivered at the recent Cloud Foundry summit in Basel.
Vlad noted that the main goal behind the benchmark “was to make sure we were not doing something completely wrong when we were containerizing, and whether there is anything we can do better.” Jeff and Vlad looked at minimal and heavy deployments of two standard cf-deployment installations:
- BOSH on Google Cloud Platform.
- A standard Helm package manager installation of the containerized SUSE Cloud Application Platform on Google Kubernetes Engine. This installation uses fissile to containerize Cloud Foundry components for running on top of Kubernetes and Docker.
Both environments remained stable, with no random failures.
“They only start to fail when they reach capacity, but you can stuff more apps in a Kubernetes-based deployment, because you can run cells across all the VMs and not just one.”
—Vlad Iovanov, SUSE
The tests were set up to get the two installations to accrue approximately the same costs as they accrued in the heavy deployments.
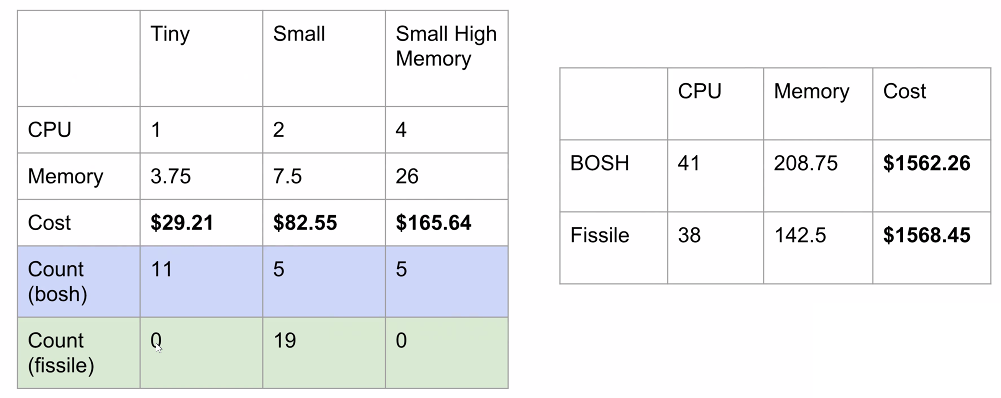 Side-by-side test configurations (Image credit)
Side-by-side test configurations (Image credit)In heavy deployments, the BOSH environment can push a few more applications compared to the fissile environment. Vlad noted that there were no issues encountered during testing. “You can keep pushing apps, they’re both stable and allow the developer to run their applications without error.”
The stability of both installations is shown in the chart below. The number of apps being successfully maintained is indicated on the left, with BOSH (blue) and fissile (green) showing similar results. The failure rates (red and yellow) of both installations are minimal.
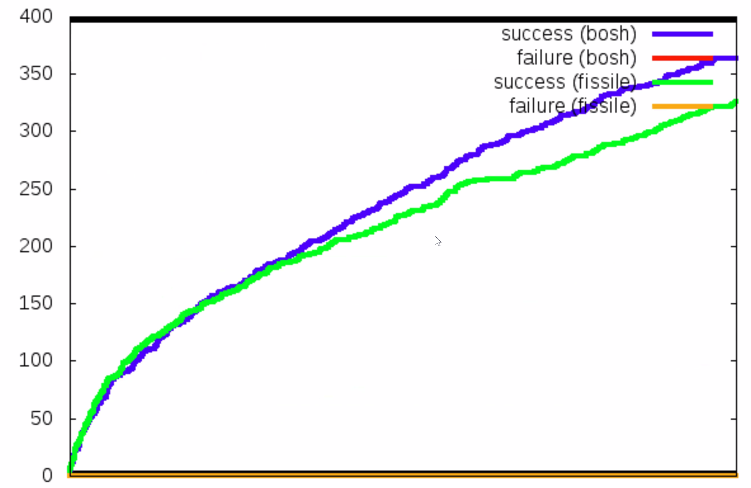 Heavy-deployment test results, the number of apps is shown on the left (Image credit)
Heavy-deployment test results, the number of apps is shown on the left (Image credit)Dr. Max of IBM, the moderator of the call, remarked that “with BOSH, you’ll reach much higher capacity before you can’t use anymore of your slack that’s built into the deployment,” while Vlad noted that “you can be much more flexible with containers and you can scale with more granularity.”
Vlad would like to create more scenarios in the future, measure performance times and related metrics, and is working on creating an open-source version of the tests, so that results may be validated and extended by anyone who’s interested in testing this comparison.
BOSH updates
Frederic Desbiens of Pivotal reported that the team is working on a vision and strategy document, which will include upcoming BOSH features that are currently in the pipeline. He also mentioned a few specific, code-level developments that are part of the overall BOSH development:
- Extend certificate functionality by removing the requirement for renewing their rotation.
- Make DNS more granular, so that users can look at the status of specific jobs rather than just at a full deployment.
- The SAP team in Germany is working on “resurrection conflict” to make it more granular for each deployment.
Frederic also noted that the CFCR team is working to enable the CFCR script authors to make more of their own decisions when it comes to the use of Kubernetes.
Runtime PMC
Eric Malm of Pivotal delivered a detailed runtime update, with several specific developments:
- The CAPI team continues to make progress on the runtime updates now available online.
- Working on developing container metrics, but would appreciate more feedback.
- Working on the CLI to accelerate transition to the API v3.
- Integration continues to advance with cf-deployment.
- Working on the container networking dynamic egress policies, for app security groups.
- Have been running rootless Garden in CPI and VM, and it’s ready to be tested out.
- Making progress toward container ID in Diego. Just declared route integrity integration, and it is stable.
- Routing continues to make integration between Cloud Foundry and an Istio release, driving toward a goal of supporting 20,000 routes through integration targets.
CF Extensions
Michael Maximilien of IBM (aka Dr. Max) reported several developments:
- App autoscaler is out of incubation and pretty much in general availability.
- Progress is being made toward highly available support of Service Fabrik.
- The team has put cflocal on hold and working to improve performance.
- The Stratos web-based console has moved to v2.2 with the new ability to add extensions.
- The Project Blockhead team is working to integrate it with the Hyperledger blockchain technology, so that users can spin up smart contracts.
CF Extensions GitHub repo | Service Fabrik’s GitHub repo | Stratos GitHub repo | Project Blockhead’s GitHub repo
The news from the CF Foundation
Swarna Podila of the CF Foundation reminded attendees of the call-for-papers deadline, which is November 30, for the upcoming Cloud Foundry Summit 2019 to be held on April 4–6 in Philadelphia. Due to the proximity of holidays, this is a hard deadline, and there will be no extensions.
Meanwhile, Cloud Foundry Days continue, with one in Shanghai on November 13, and the other one upcoming in Seattle on December 10. Furthermore, webinars are being held on Kibosh on November 15 and one on Application Runtime versus Container Runtime on November 29.
The Foundation team has also worked diligently to post content on YouTube from the recent European summit in Basel with 114 videos already available.
What’s next?
The year will be summed up during the final CAB call of 2018 on Wednesday, December 19, from 8 a.m. to 9 a.m. Pacific time. As always, the call is open to all, and the best way to join in is through the Cloud Foundry Slack channel.











