Cloud Foundry Advisory Board Meeting, Aug 2016: CF Days Launched

Remember the joke about the prominent technology company that was so focused on straightforward engineering it was claimed that if it opened a sushi bar it would name it “Restaurant for Cold, Dead Fish”?
Oh, you don’t? I see.
Cloud Foundry Days
In any case, the Cloud Foundry Foundation and its members continue to try to avoid that trap, as this open, collective engineering effort madly adds features every month while at the same time working to capture the imagination of potential customers.
Thus, the creation of Cloud Foundry Days was announced at the most recent CF Community Advisory Board (CAB) call on August 10.
This new initiative envisions a series of meetups, or “super meetups” as they may be accurately called, in several Asian cities during the remainder of 2016. The CF Foundation’s Stormy Peters said this program could then potentially roll out to the rest of the world in 2017.
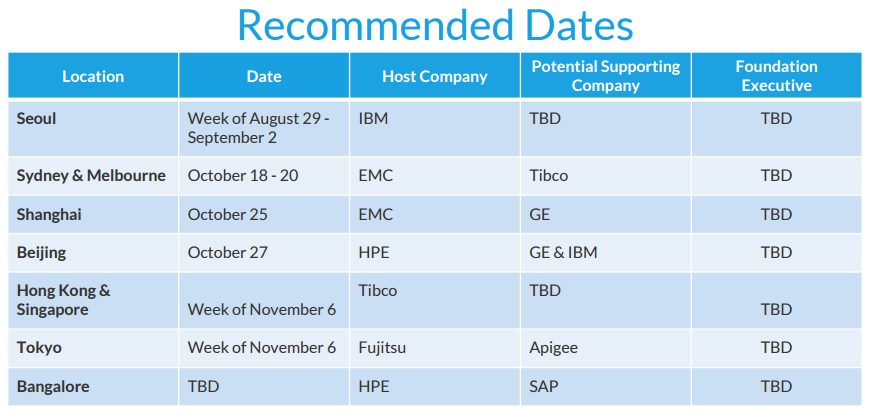
The big dogs within the CF Foundation are mentioned as sponsors of this series. Potential locations and sponsors are shown in the following slide:
The complete vision of Cloud Foundry Days is available at the CF Foundation’s website.
The call also featured discussion about the idea of a “Hack Day” to precede the rapidly approaching Cloud Foundry Summit in Frankfurt, Germany on September 26–28. We’ll keep you updated as this conversation progresses. Anyone who’s interested in participating in this should contact the CF Foundation.
Back to the fish—several updates from the project managers were featured during the call as usual, as listed below. The meeting was, as usual, managed by Michael Maximilien (Dr. Max) of IBM.
Project Manager reports
CLI (Dies Köper, Fujitsu)

- Released CF CLI 6.21.0, adding support for defining TCP routes and HTTP routes with paths in app manifests and updated message translations.
- Close to releasing CF CLI 6.21.1, fixing community reported bugs including a regression around ANSI coloring in CF logs on Windows, and digitally signing the Windows binaries.
- Completed (on a branch) internal Golang imports change to code.cloudfoundry.org/cli.
- Started (on a branch) refactoring towards the implementation of the
cf helpredesign. - Considering to remove the Loggregator consumer library (see plan here) soon after releasing the new help.
- Progressing well on investigation of software repo management options to enable users to download and update the CF CLI using apt-get.
Grootfs (Will Pragnell, Pivotal)

- Shipped v0.1.0 with basic creation/deletion of file systems from a disk based rootfs.
- Now working on pulling Docker images from remote registries and applying disk quotas to file systems.
Garden Core (Julz Friedman, IBM)

- Released v0.341.0 of garden-linux with some fixes to allow garden-linux to work with 4.4 stemcells.
- Released v0.4.0 of garden-runc with major improvements including:
- Security: enable AppArmor protection for unprivileged containers. (This is a big deal!)
- Integration: use “Create/start” split to enable better integration of container-to-container networker.
- Integration: allow exit code to be retrieved from processes after Garden restart (important for Concourse CI).
- Operability: remove iodaemon! (A big source of support headaches now gone.)
- Tracked down flakiness in inigo tests.
- Investigation around iodaemon issues in garden-linux on some environments.
- Begun exploration of next main focus of work, ‘rootless garden-runc,’ hope to be able to fully remove the need for rootto run garden-runc.
Garden-Linux repo | Garden-RunC repo
Greenhouse (David Morhovich, Pivotal)
- Revert magical CUPS behavior.
- Write temp files in container directory.
Diego (Eric Malm, Pivotal)

- Deployed 20-cell cluster in “Flintstone” environment, running BBS API-based tests against it.
- Working on new tooling in diego-perf-release to push CF apps for later tests.
- Various logging and metrics improvements to support analysis of experiments.
- Continuing work on story to have cell download cache persist across restarts.
- Added manifest-generation script for windows-cell BOSH deployment.
- Continuing basic development of cfdot: added usage messages, adding TLS-config flags.
- Added opt-in mechanism to derive cell AZ assignment from Azure fault domain.
Abacus (Dr. Max & Jean-Sebastien Delfino, IBM)

- Various bug fixes.
- UI work started by SAP India.
Routing (Shannon Coen, CF Foundation)

- Routing components, including gorouter, upgraded to Golang 1.6. Final release of routing-release forthcoming.
- Picked up performance track again as team strength allows.
Release Integration (Amit Gupta, Pivotal)

- CATS-as-a-Concourse task validates input.
- Nats-release pipeline now fully testing along with rest of Cloud Foundry and cutting final releases.
- BOSH-2.0 CF manifest now gets all bits from bosh.io, and only buildpacks still come from cf-release.
- Nats-release already receiving helpful PRs.
- Starting work on streamlining CATS for better parallelizability and consistency.
- Pipeline cleanup and refactoring.
Infrastructure (Amit Gupta, Pivotal)
- Finished extracting postgres-release and building out pipeline.
- Wrapping up etcd TLS zero-downtime upgrade tests.
- Working on parallelizing and speeding up consul-release and etcd-release pipelines.
- Working on bbl supporting upcoming BOSH CLI.
- Working on bbl supporting tagging resources for better identifiability.
Runtime OG (Michael Fraenkel, IBM)
- Fixed a memory leak when downloads fail during staging.
- Evacuation waits for staging to complete.
- Send a 503 error (Service Unavailable) when attempting to stage during evacuation (waiting on CAPI bump to cause a retry).
- Inactivity timeouts set to 30 seconds instead of 300 seconds.
Loggregator (Jim Campbell, Pivotal)

- Support for dynamic IPs.
- Building load test infrastructure to test Metron->Doppler TCP upgrade.
- Using Concourse, starting from a stub, build up AWS deployment, run load test, run a deployment, and tear down environment.
- Generally useful for CF?
- Testing very large log messages (100 MB).
- Metron Windows now in our CI pipeline.
CAPI (Nicholas Calugar, Pivotal)

- V3 migration is nearly code complete, upcoming stories are mostly verification.
- Publishing capi-release on bosh.io.
- Merged BITS service PR as experimental, disabled by default.
- Cloud Controller supports new cloud_controller.admin_read_only for all GET endpoints.
- User-specified buildpack is encrypted at rest, creds in buildpack URL masked for GET requests.
PERSI (Ted Young, Pivotal)

- Completed v2.10 of Volume Services.
- Awaiting feedback for Docker pull request.
- Started EFS reference Driver/Broker for AWS.
- Investigating Snapshot/Restore.
- Refactoring Cell API to enable scheduling experiments.
Container Networking (Usha Ramachandran, Pivotal)

- Began effort to consolidate network interfaces inside application containers.
- The goal is to only have eth0 and loopback. eth0 will be on the container network, able to receive port-forwarded traffic from the gorouter, and able to reach the Internet via on-cell masquerade.
- This is a large effort and is still in flight.
- Improved system component logging. Now forwarding to syslog, consolidating per-container CNI logs in one place.
- Added iptables logging for packet drops.
Bits-Service (Simon Moser, IBM)

- Bits-Service successfully merged and integrated in the CAPI release.
- Mainly working on leftover chores from that (e.g., adjusting the pipelines and tests).
Services Core (Marco Hochstrasser, Swisscom)

- Cf-mysql-release v27 delayed due to snafu in BOSH pre-start.
- Investigating if/how to move SST back out of pre-start.
Buildpacks/Stacks (Stephen Levine, Pivotal)

- Concourse logs public
- go-buildpack—1.7.9–1.7.12
- ruby-buildpack—1.6.20
- buildpack-packager—2.2.9–2.3.1
- nodejs-buildpack—1.5.17–1.5.18
- php-buildpack—4.3.15–4.3.17
- staticfile-buildpack—1.3.10
The next call is scheduled for Wednesday, September 14 at 11 a.m. Pacific Time. Should be plenty more fish on the menu by then.
Some links
The project manager updates can also be found at GitHub, which has several related areas in which interested community members can be kept apprised of developments.
There’s also a Slack channel in use, including a sub-channel focused on the CAB calls.