Ensuring Security Across Kubernetes Deployments
Challenges with security
Kubernetes is one of the most adopted open-source container orchestration systems today. Organizations from cloud-native companies to banks are adopting Kubernetes on public platforms, such as Azure Kubernetes Service, Google Kubernetes Engine, etc.
In an interview with TechCrunch, Amir Ofek, CEO at Alcide, noted that while the flexibility of Kubernetes enables DevOps to have a much easier time building their clouds, it also opens up plenty of gaps in security.
“In Kubernetes, it is quite simple for hackers to take control of your account. It is a very open infrastructure as it was intended to be, but that is what hackers are also taking advantage of.” —Amir Ofek, Alcide
According to Gadi Naor, CTO at Alcide, Kubernetes out-of-the-box is optimized to make things work, but not necessarily to work in a secure manner. During a Kubernetes meetup last December, Gadi highlighted some of the problems and challenges in security.
- When running images in Kubernetes, how can we be certain that we are not running images with malicious code embedded in them?
- How can we ensure that containers running in Kubernetes are configured properly?
- How do we prevent tainted continuous integration (CI)/continuous delivery (CD) deployments?
- Is it possible to scan Kubernetes deployments for potential security vulnerabilities?
“Kubernetes is a very sophisticated and well architected piece of software. It enables a lot of flexibility on how you run, scale, and orchestrate things, but it requires a relatively good understanding of Kubernetes itself.” —Gadi Naor, Alcide
A Kubernetes security checklist
Similar to any other software, Kubernetes can become vulnerable due to misconfiguration. During the meetup, Gadi provided some guidelines for securing the different layers in Kubernetes deployments.
- Istio control plane. Make sure the resources being deployed to Istio go through certain assertions (e.g., in Istio, each service being deployed should have mutual transport layer security enabled by the configuration).
- Kubernetes control plane. Configure who should and should not have access to the API server.
- Worker nodes. Make sure that all the worker nodes are running the latest patches.
- Cluster infrastructure. Use annotations to configure the underlying cloud provider (e.g., when spinning up load balancing services, which expose the cluster to the outside world, you can place annotations on the service resource, and it will tweak how the load balancer is going to be provisioned).
- Workloads. Create a whitelist for privileged workloads that require access to the underlying host.
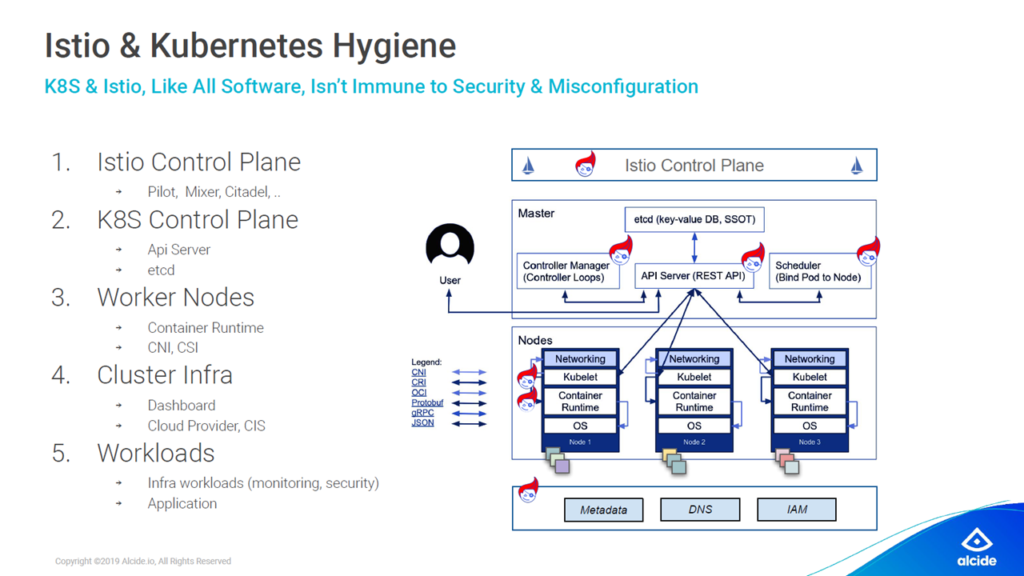 Configure security at different layers (Image credit)
Configure security at different layers (Image credit)In addition to the above-mentioned guidelines, Gadi added a more conclusive list of security best practices and compliance checks for Kubernetes deployments.
 Security and compliance checklist (Image credit)
Security and compliance checklist (Image credit)With such an extensive scope of best practices and compliance checks, Gadi advises prioritizing the registry whitelist, as this can minimize the damage to a cluster in case of a security breach.
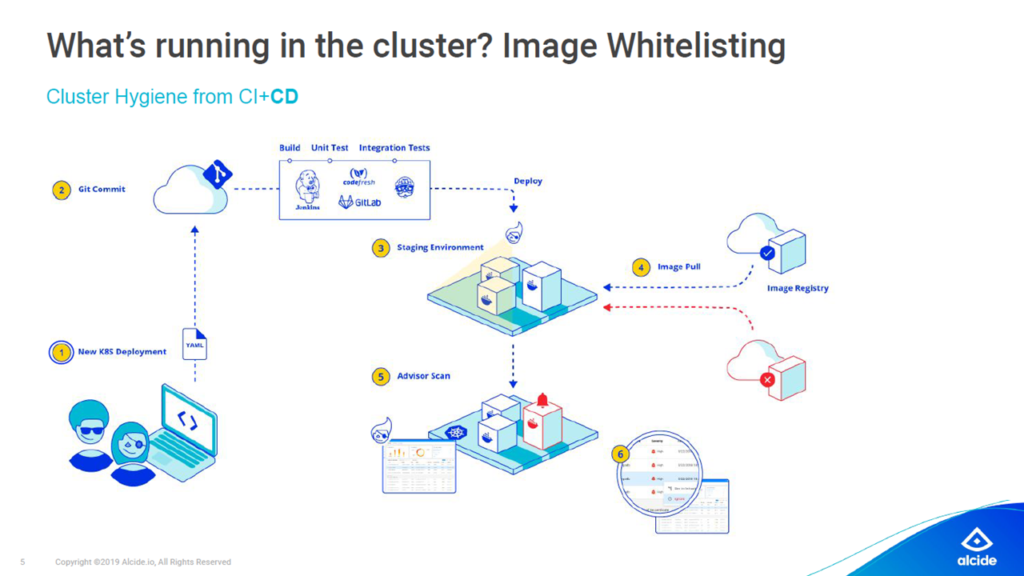 Image whitelisting prevents containers from running in the privileged mode (Image credit)
Image whitelisting prevents containers from running in the privileged mode (Image credit)“If I were to prioritize, I would start with the registry whitelist to make sure that things are not running privileged. It is paramount to ensure that even if there is an application breach, the damage in under control.” —Gadi Naor, Alcide
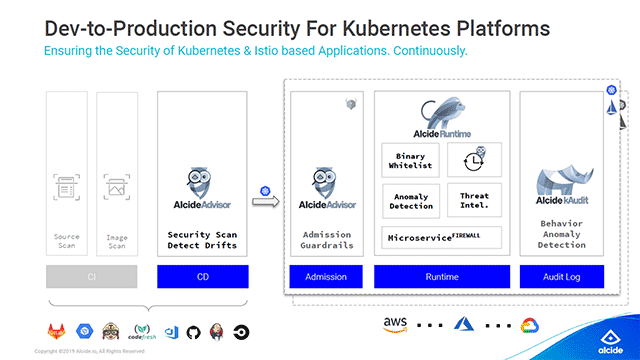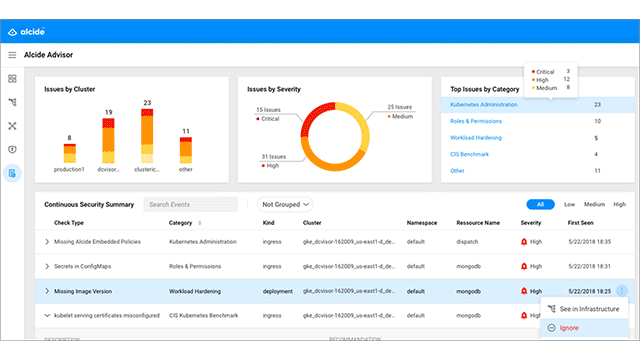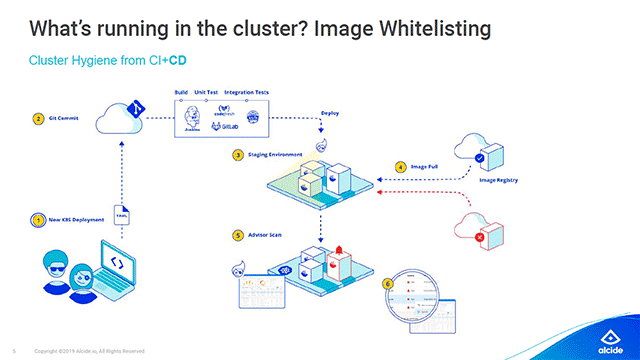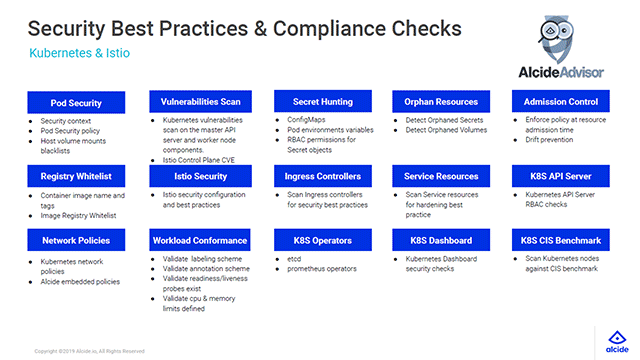
Dev-to-production security
To minimize the effort needed to secure Kubernetes deployments, Alcide developed a security platform, which delivers guardrails for DevOps, as well as ongoing threat detection and protection for security teams.
The solution includes three modules. The first is Advisor, a multi-cluster vulnerability scanner, which provides:
- snapshots of the cluster’s risks and hygiene, as well as a detailed list of misconfigurations
- detection of drifts and noise reduction by putting an emphasis on the cluster hygiene delta
- real-time prevention of misconfigurations and blocking tainted CI/CD pipelines
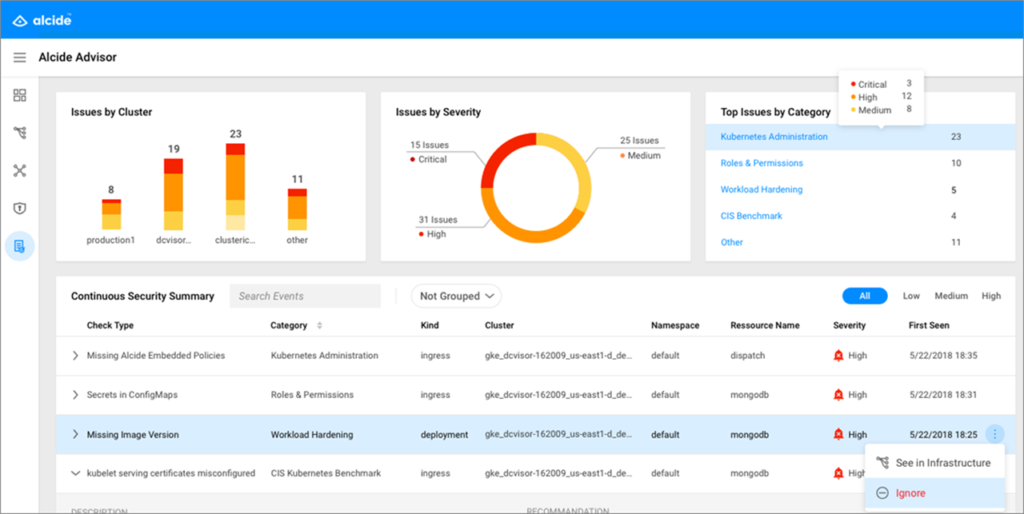 The Alcide Advisor dashboard (Image credit)
The Alcide Advisor dashboard (Image credit)The next module, Runtime, embeds security and compliance policies into microservices. Runtime also enables behavioral-based anomaly detection to protect your clusters against attacks that are either overlooked or undetected by traditional layers of security.
Lastly, kAudit identifies anomalous Kubernetes behavior by analyzing audit logs. In this manner, it is able to detect issues, such as security policy violations, RBAC misconfigurations, and vulnerability exploits in the Kubernetes API server.
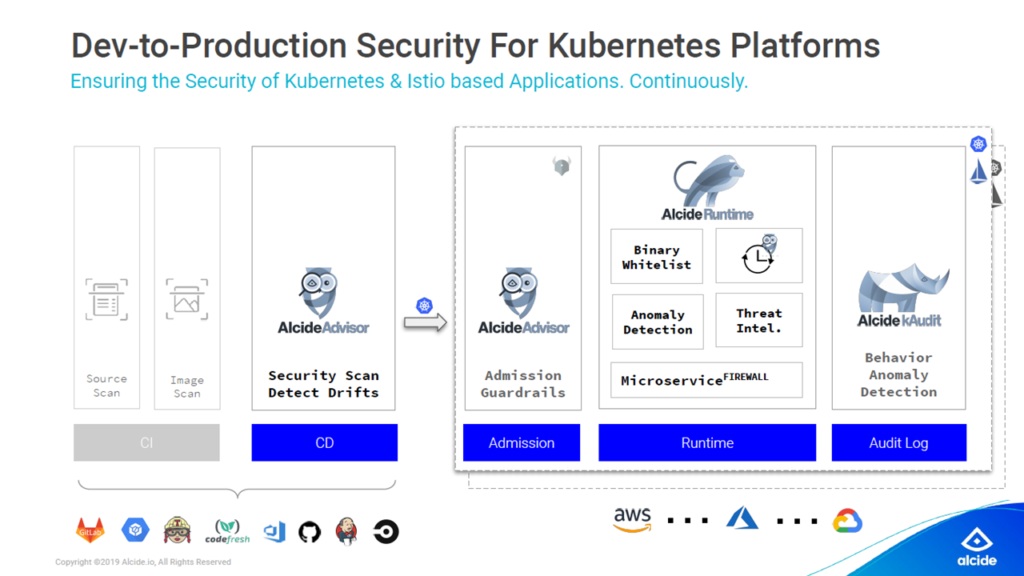 Alcide scans from CD to production audit logs (Image credit)
Alcide scans from CD to production audit logs (Image credit)“We scan all of the designs in the CD stage and flag out any security issues in violation of predefined policies. When you move into production, we monitor all of the logs within the Kubernetes infrastructure. We also provide a service that protects all of the microservices, such as firewalls for your workloads.” —Amir Ofek, Alcide
To learn more about how to use Alcide, check out the project’s tutorials. Additionally, more information about how to secure clusters is available in the Kubernetes official documentation.
Want details? Watch the videos!
In this video, Gadi Naor provides best practices for securing Kubernetes deployments.
Below are Gadi’s slides from the meetup.
In this video, Amir Ofek explains how Alcide provides security for Kubernetes.
Further reading
- Tips for Implementing Shift-Left Security on Kubernetes
- Improving Security for Kubernetes Deployments at Scale
- Rule-Driven Automation on Kubernetes with Autopilot Monitoring
About the experts












