Blockchain Security: Choosing a Platform Is Only the First Step
Security threats everywhere
Since last year, there have been several discussions surrounding blockchain technology—ranging from adoption predictions to requirements from the financial industry. There was also increased interest and investment in the development of the technology with the inception of the Hyperledger Project in December 2015.
With both financial and non-financial institutions adopting distributed ledgers and with the release of Hyperledger Fabric v1.0, keeping blockchain networks secure is the next step.
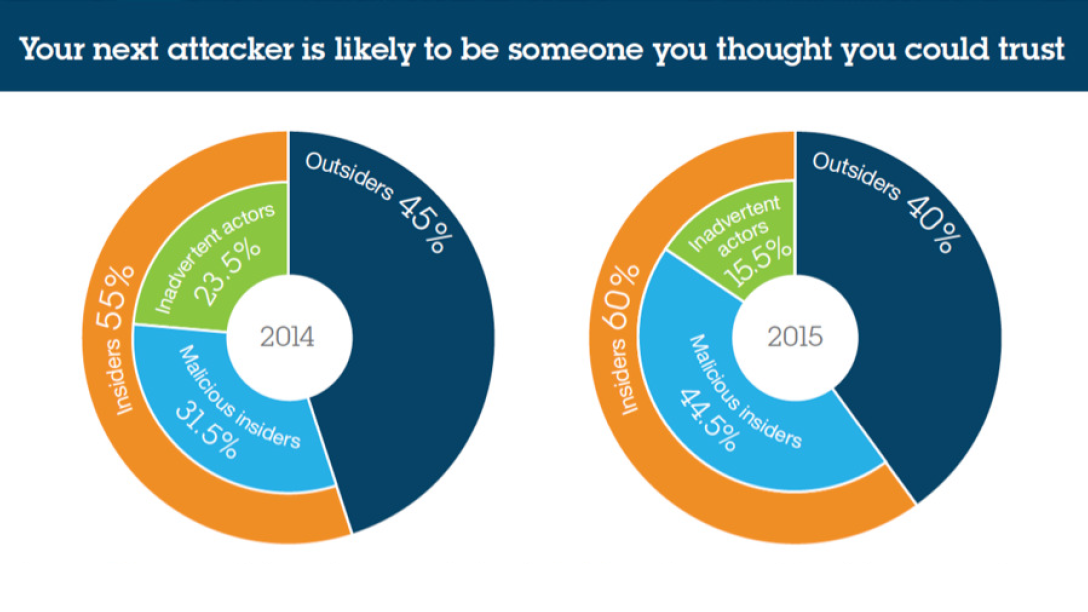 Source
SourceThe figures are self-explanatory. For instance, Ethereum lost millions due to a hack last year. At the same time, according to a an IBM X-Force report, 60% of attacks are from internal threats.
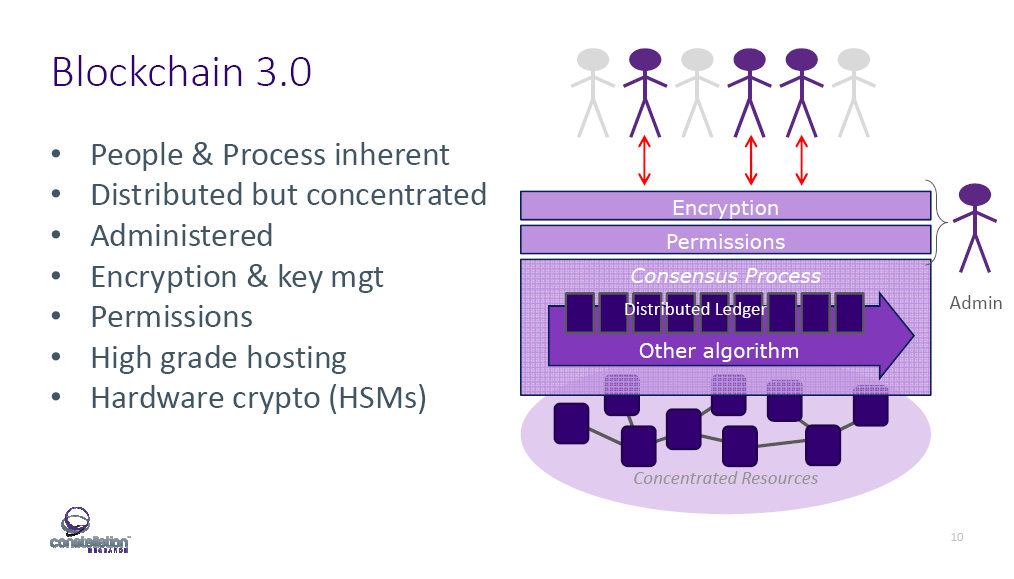
It’s hard to disagree with Constellation Research’s Steve Wilson, who states that “confidentiality is not trivial.” At IBM InterConnect 2017, he presented the idea of “Blockchain 3.0,” describing it as the next generation of the distributed ledger model, which will require more security than ever.
“What does Blockchain 3.0 look like? It seems like people and processes are in the mix again. It’s not like the original public blockchain where we pretend people and processes don’t matter.” —Steve Wilson, Constellation Research
A secure business network with Hyperledger
Improving on current blockchain technology, IBM wants a blockchain that is “open, trusted, and for business.” This is realized by collaborating on Hyperledger Fabric v1.0—an open-sourced private, permissioned blockchain technology.
According to IBM’s Jerry Cuomo, Hyperledger Fabric v1.0 is built on a trust model that is democratic with permissions and consensus, tamper-proof, and is auditable to better emulate how real businesses interacts. Transactions within this model would proceed as follows:
- Participants are issued a cryptographic membership card which represents their identity within the blockchain network.
- This membership card grants you access to see transactions in the ledger that pertain to you and only you.
- Auditors may be granted membership that allows them to see a little more of the ledger to ensure that transactions are in compliance.
- Trust is further built through the process of consensus. Transactions are first proposed to members of the network. These transactions are then voted on through the process of consensus.
- When the majority agree, consensus is reached. Then and only then, will the transaction be committed to the ledger and it cannot be erased.
“Hyperledger Fabric v1.0 is capable of transacting at rates way over 1,000 transactions per second.” —Jerry Cuomo, IBM
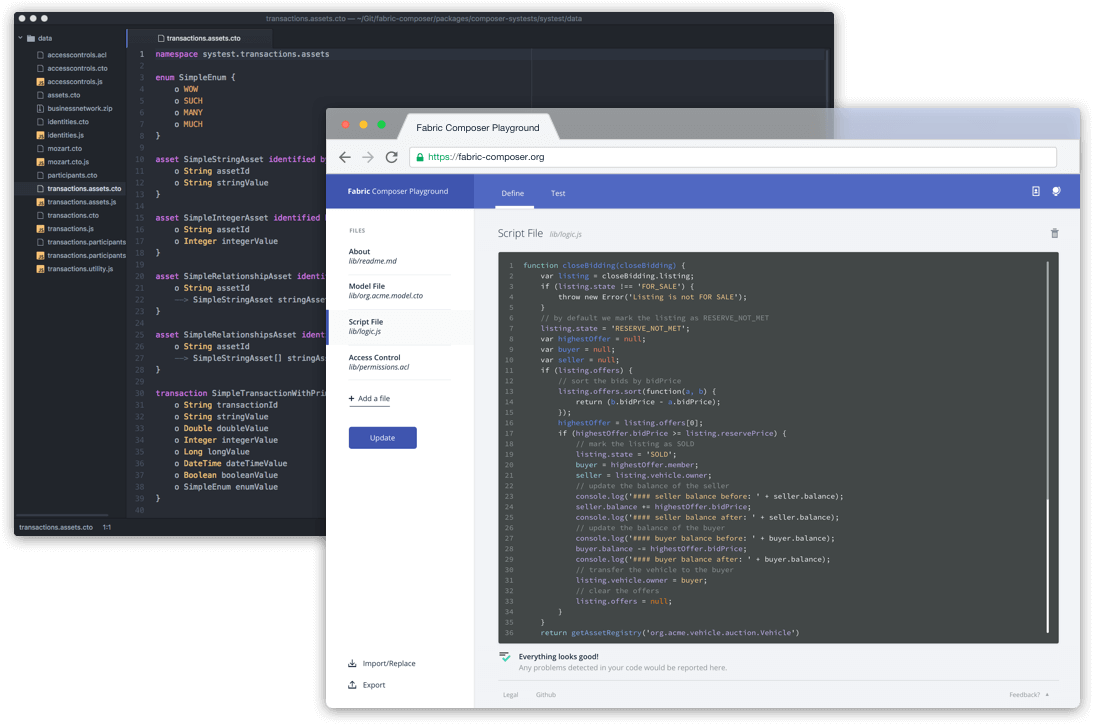
Jerry also introduced Hyperledger Fabric Composer, a new tool that “allows business users and developers to speak the same language, thereby accelerate the creation of busineses solutions from days to minutes.”
With Hyperledger-based platforms and Fabric Composer, blockchain creation and management has been simplified, as users can:
- Rapidly develop a blockchain solution
- Find and govern blockchain networks
- Operate those networks with security and do it all at scale
- Analyze into those networks by peering in to gain additional insight
A reference architecture for secure blockchain
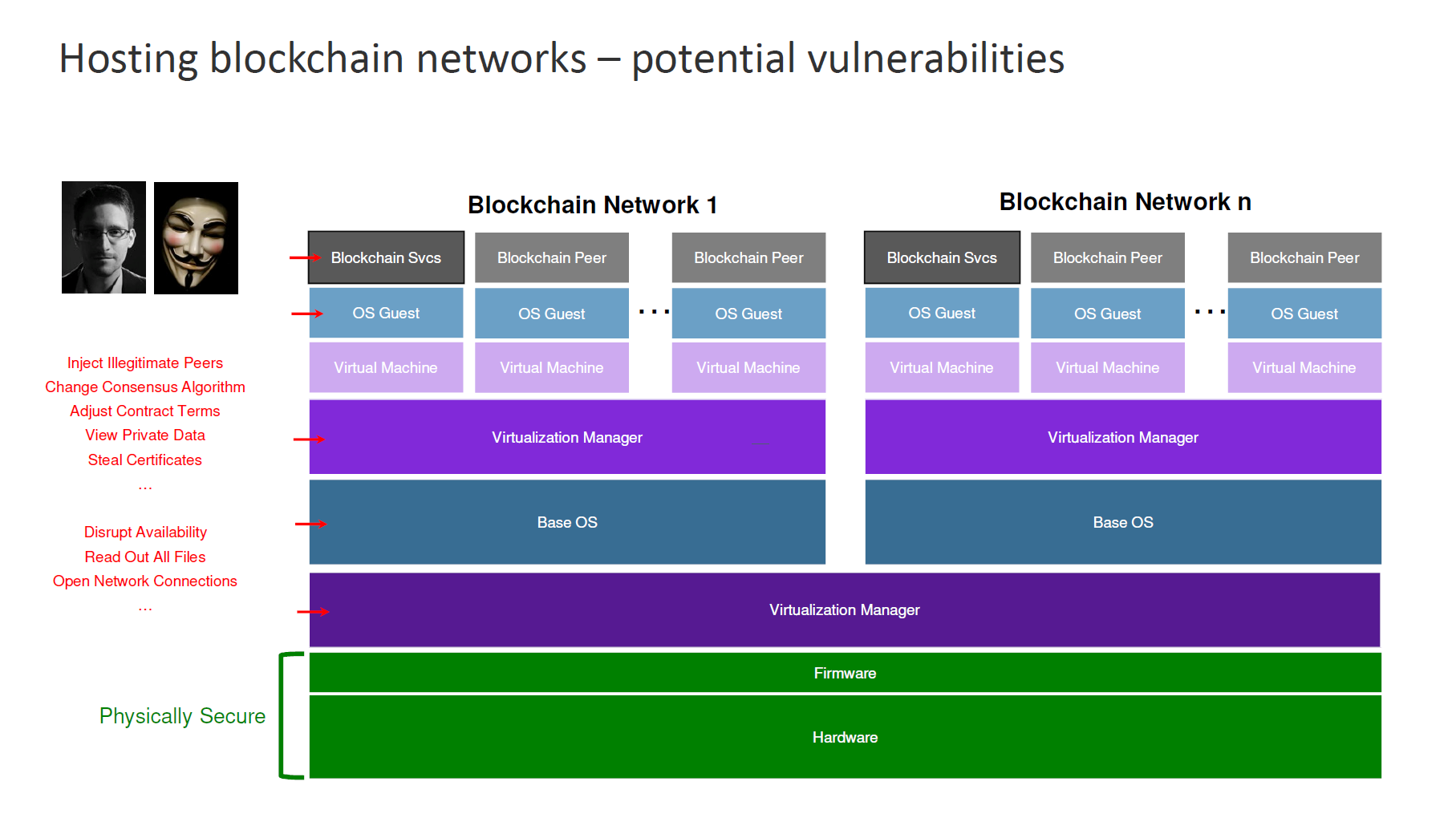
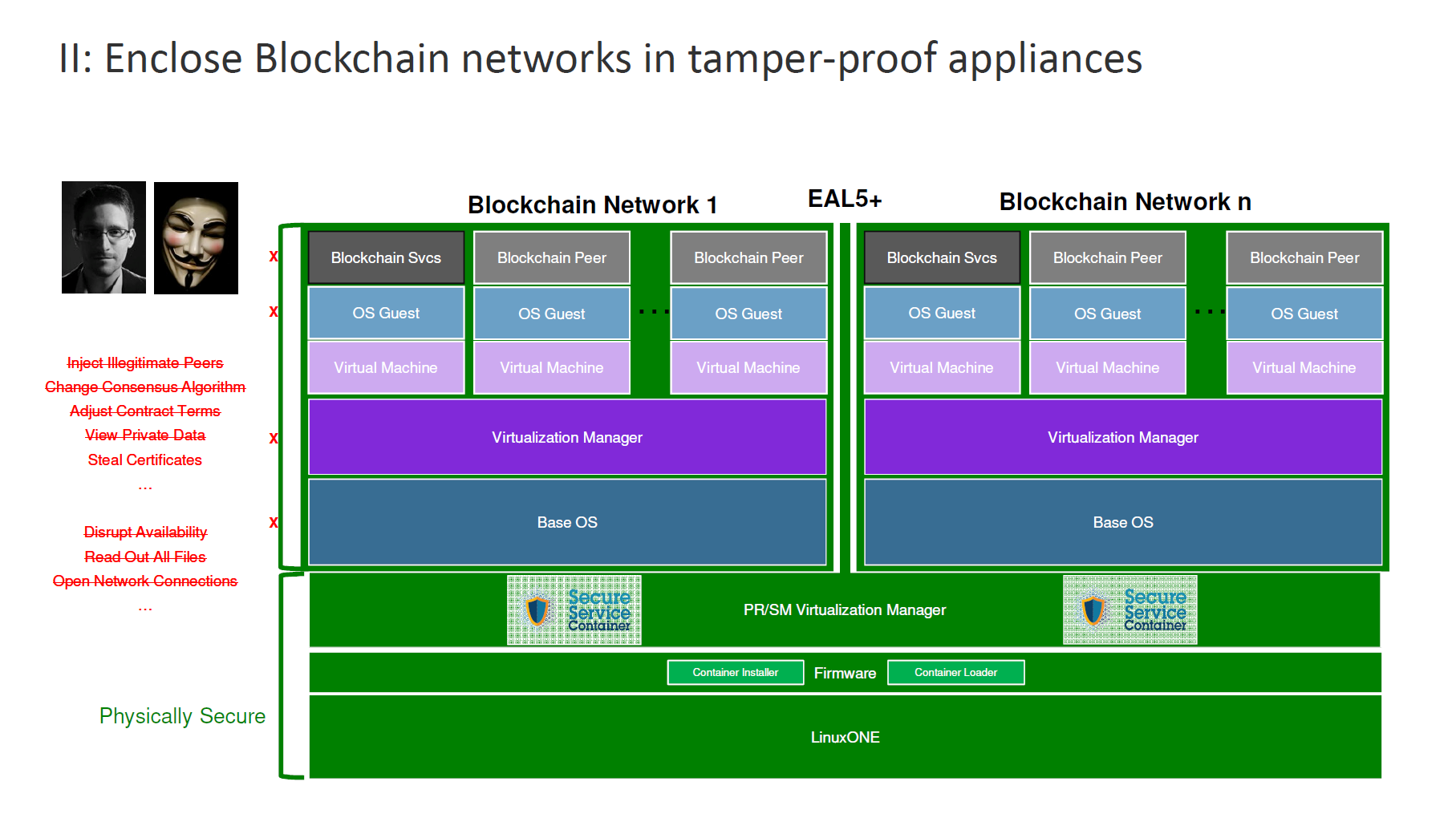
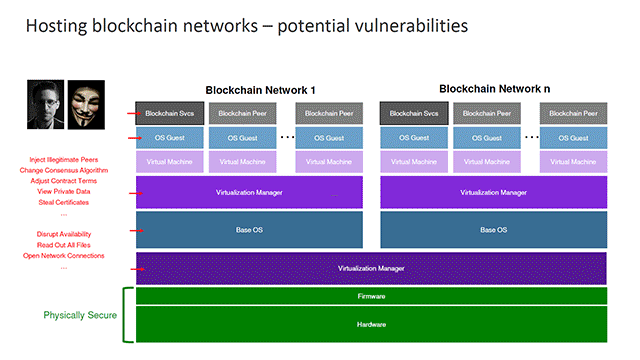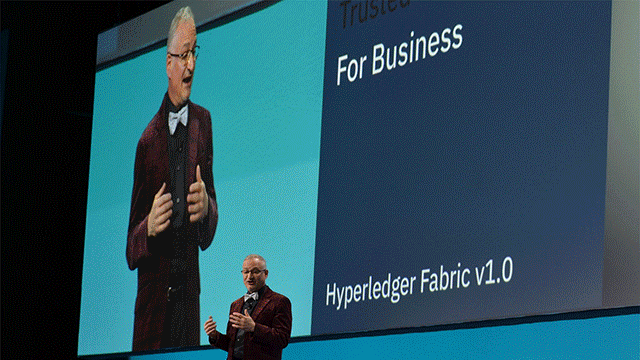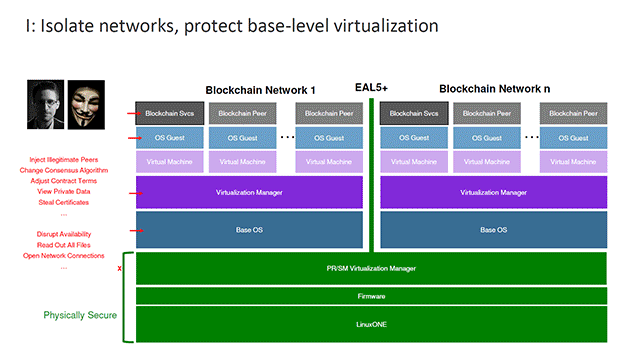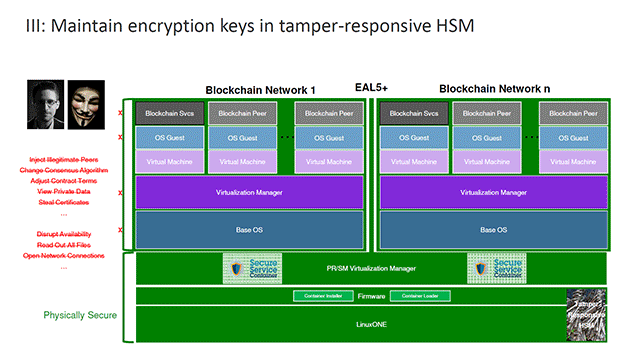
However, according to other speakers at IBM InterConnect, “choosing a fabric is just the first decision,” and more efforts are needed to secure the blockchain network. To explain this in detail, IBM’s Paul DiMarzio presented a typical architecture for a blockchain stack.
In this configuration, the hardware and firmware are physically secured, but everything else in the software level is vulnerable to attacks.
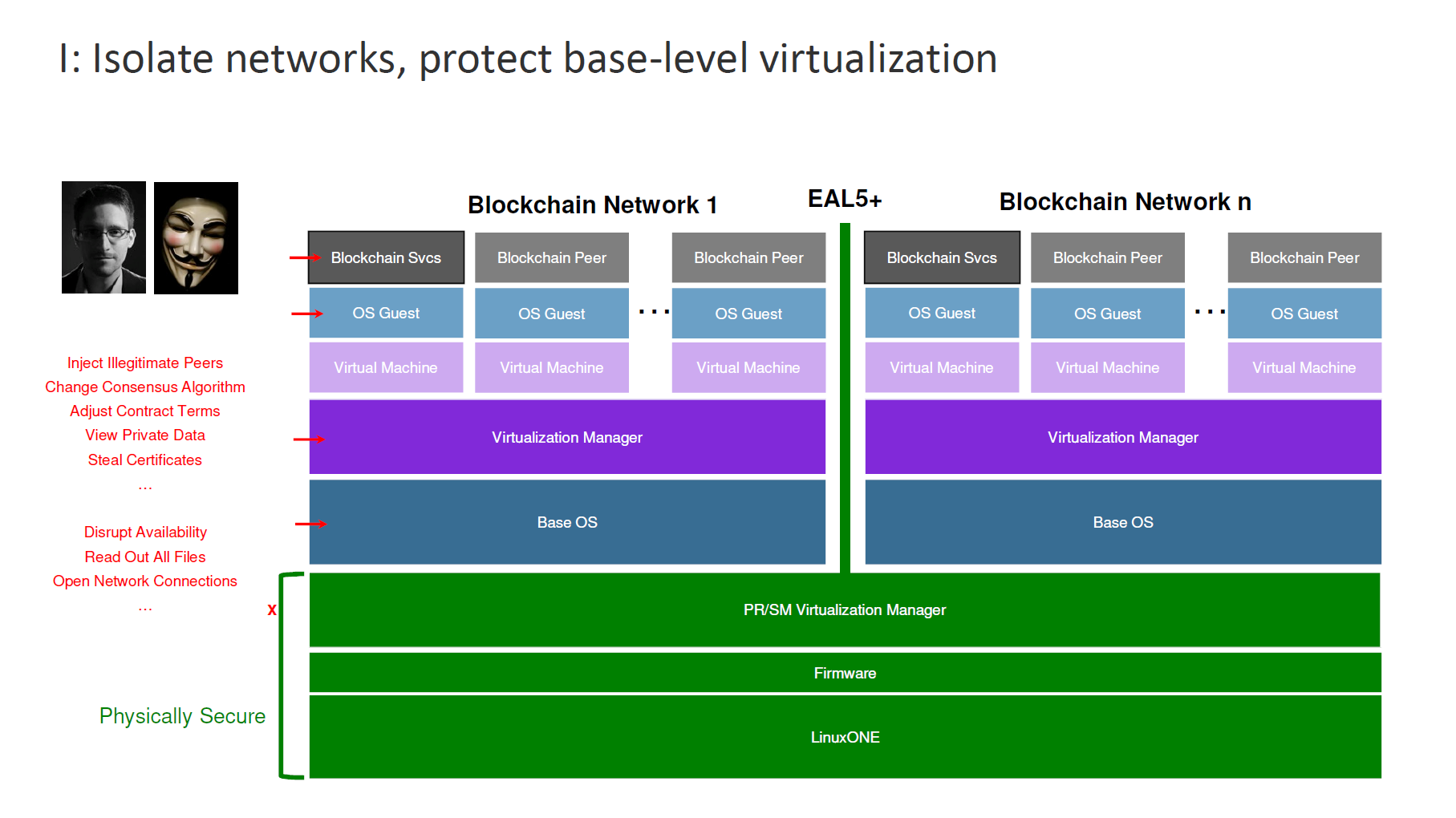
To achieve the same level of security at the hardware level, IBM adds several layers of security to slowly push up that protection to the very top of the stack. In this step, PR/SM virtualization technology is used to protect different partitions in the system.
Next is building Secure Service Containers into the virtualization layer now extends security up to the very top of the stack. (Read the next section for more on Secure Service Containers.)
“By building Secure Service Containers, we can entirely encapsulate a blockchain network and make it such that anybody even at the highest level of credentials can disrupt it.” —Paul DiMarzio, IBM
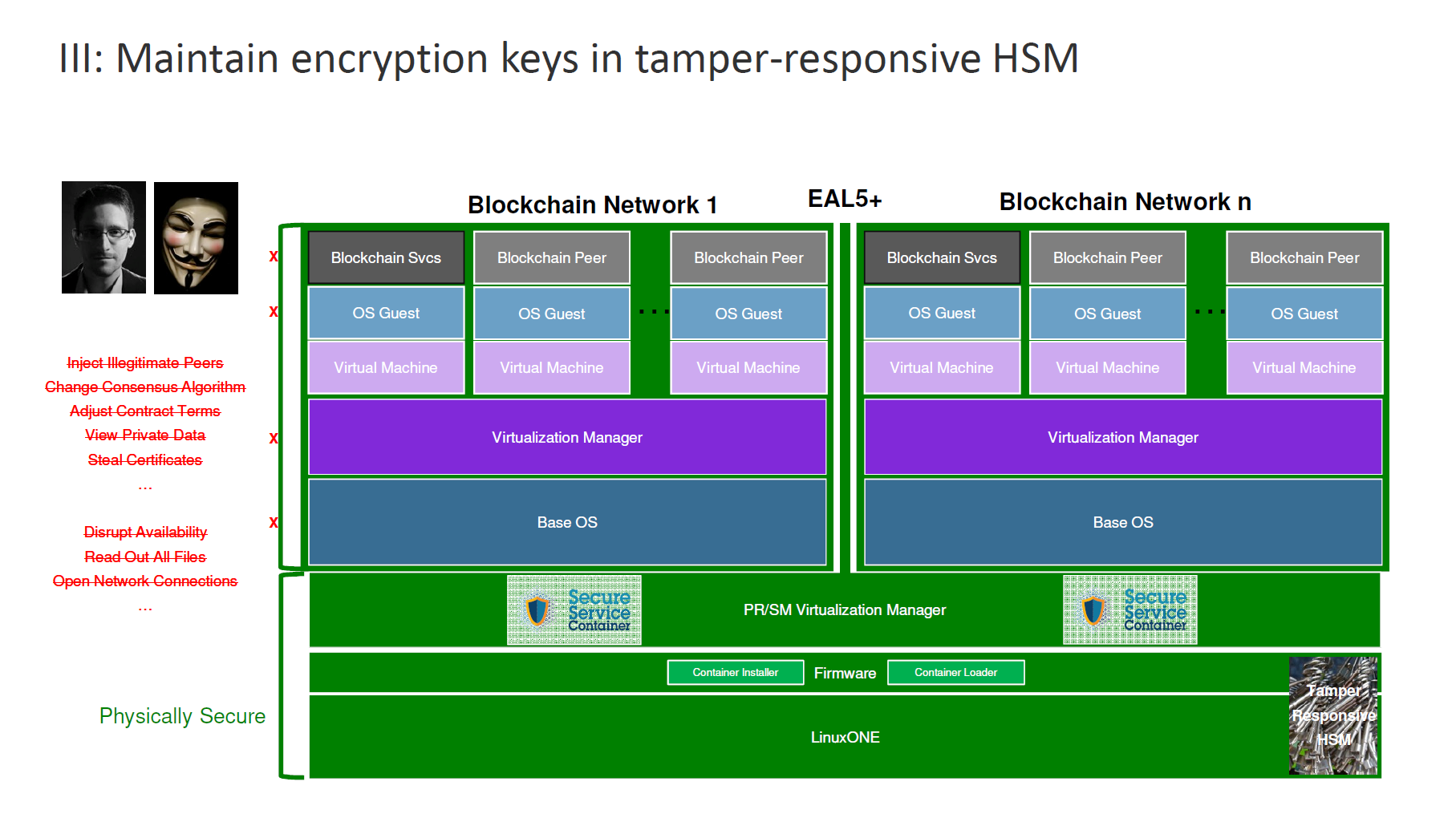
Finally, through the use of tamper-responsive hardware security modules, the system is protected from certificates theft. Attempts to steal the keys will cause them to self-destruct.
Relying on Secure Service Containers
To secure the blockchain network itself, IBM makes use of Secure Service Containers. IBM’s Paul DiMarzio details how it protects blockchain software, chain code, and data:
- Root users and system administrators cannot access blockchain contents.
- Malware cannot self install in the container.
- Encryption keys are protected.
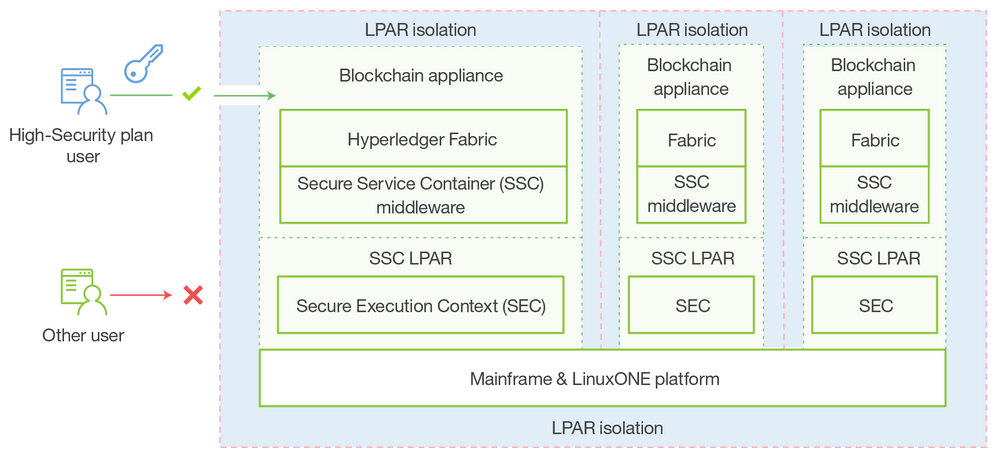 Source
Source“It’s a trusted environment, because it’s encrypted and signed in firmware so that we know if it’s been tampered with,” explained Paul. “You can’t inject malware. You can’t inject changes without the system knowing and stopping it. Once it’s running, operators have no access to it.”
Secure Service Containers ensure that:
- No system admin access. Once the appliance image is built, OS access (SSH) it not possible.
- Only remote APIs are available.
- Memory access is disabled.
- Disks are encrypted.
- Debug data (dumps) is encrypted.
“It’s the ability to effectively put an impenetrable blockbox around any system, any application from the virtualization software all the way up to the application.” —Paul DiMarzio, IBM
Blockchain securing diamonds
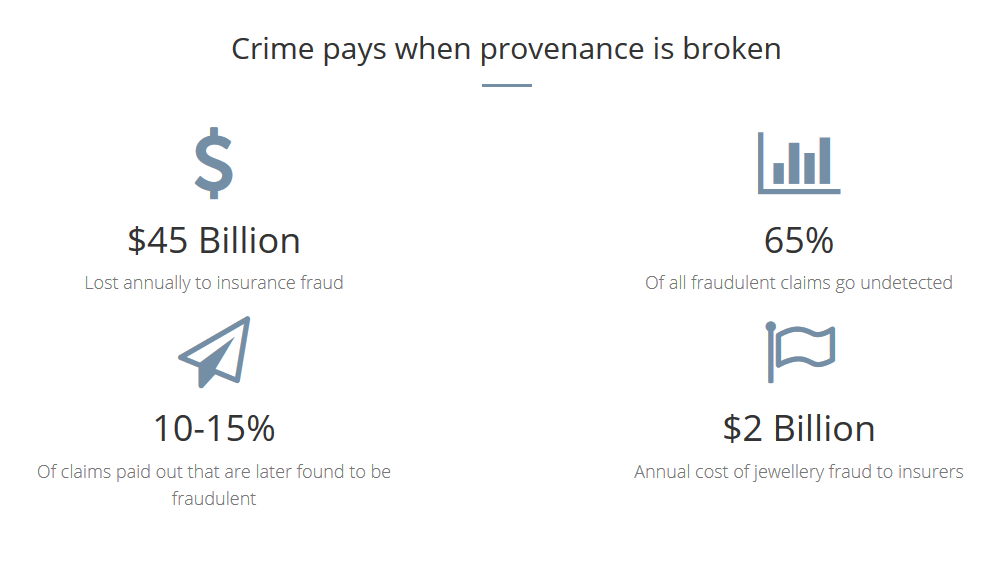
Leanne Kemp told the story of Everledger and how it was able to develop a trusted platform to protect the diamond industry from threats such as fraud, document tampering, synthetic stones, conflict stones, black markets, and double financing.
All of these issues were rooted on a lack of visibility and provenance along the supply chain. This was underpinned by a paper-based certification system that was vulnerable to tampering.
Using Hyperledger-based IBM Blockchain on LinuxOne, Everledger built a platform that brought greater transparency to the open market places and global supply chain by ensuring that the authenticity of the asset is secured and stored among all industry participants. “We integrated the supply chain onto the same digital network creating a single version of the truth for all parties involved in the diamond trade,” said Leanne. “We shared records visible across the industry participants.”
“The blockchain is re-imagining the world’s luxury goods supply chain. —Leanne Kemp, Everledger
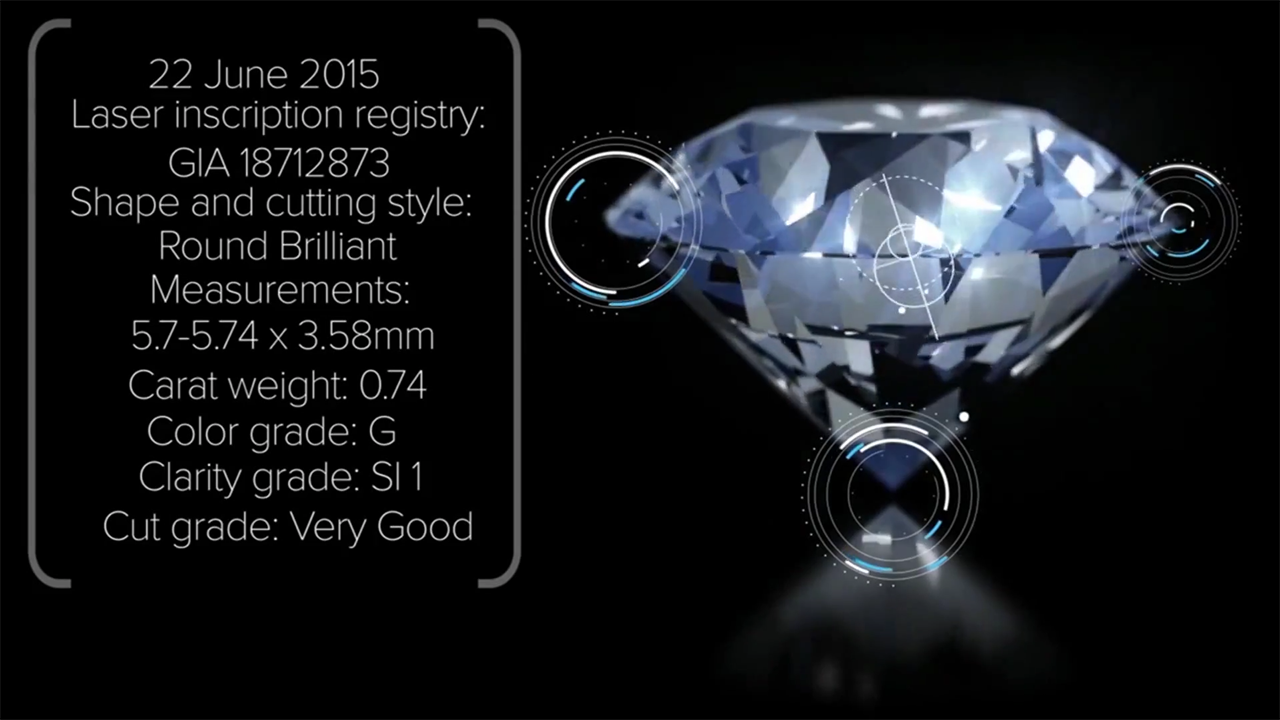
With blockchain, Everledger is able to set meta data to identify diamonds, essentially creating a digital thumbprint for each stone. This information is then used to create immutable certificates that identify individual diamonds in the market and can be used by participants on a supply chain to form provenance and verify authenticity.
Leanne is hopeful that the success Everledger has found with blockchain will eventually expand beyond diamonds and onto other luxury goods.
Related reading
- IBM: Blockchain to Transform IoT, Supply Chains, and the World Around Us
- IBM InterConnect: Bringing in Secure, Hybrid, and Multi-Cloud Infrastructure
- How Hyperledger Fabric Delivers Security to Enterprise Blockchain
- Hyperledger’s Fabric Composer: Simplifying Business Networks on Blockchain
About the speakers